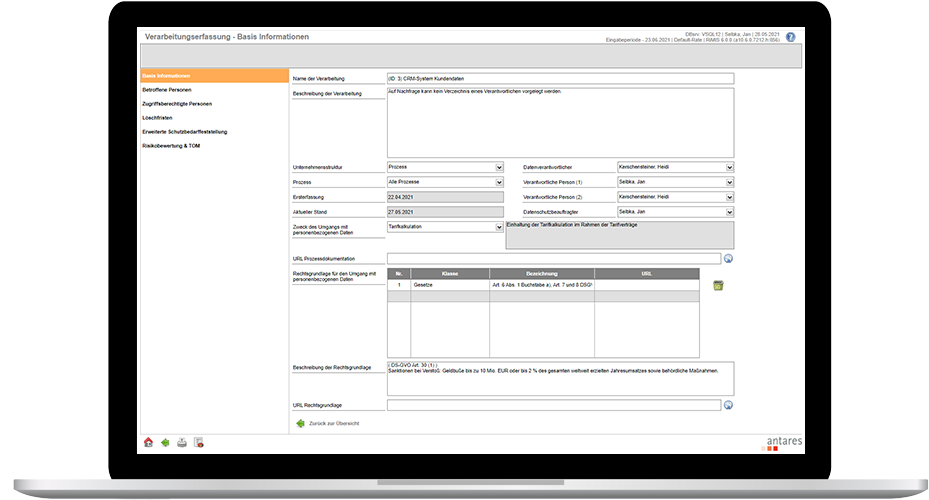
antares RiMIS® DPMS
We help you to master the new requirements of the General Data Protection Regulation for commissioned processing in your company and to establish new processes and structures. To do this, it makes sense to integrate the data protection guidelines into the existing information security management system (ISMS). This creates a holistic data protection management system.
Our DSMS based on the Basic Regulation and ISO 27001 or/and IT-Grundschutz establishes recognized procedures with which processes and guidelines are methodically introduced in a company. These guidelines enable the timely identification of risks for data protection breaches. The aim here is to use all technical and organizational measures to enable their management, control and permanent improvement. The guarantee of confidentiality, integrity, availability and resilience of IT systems and services with regard to data processing is implemented in a similar way to an ISMS.

Reliable protection of company data

Sustainable, holistic risk minimisation

Safeguarding the company values

Audit-proof documentation of the activities

Compliance with business partners, customers, etc.
Connection between DPMS and ISMS
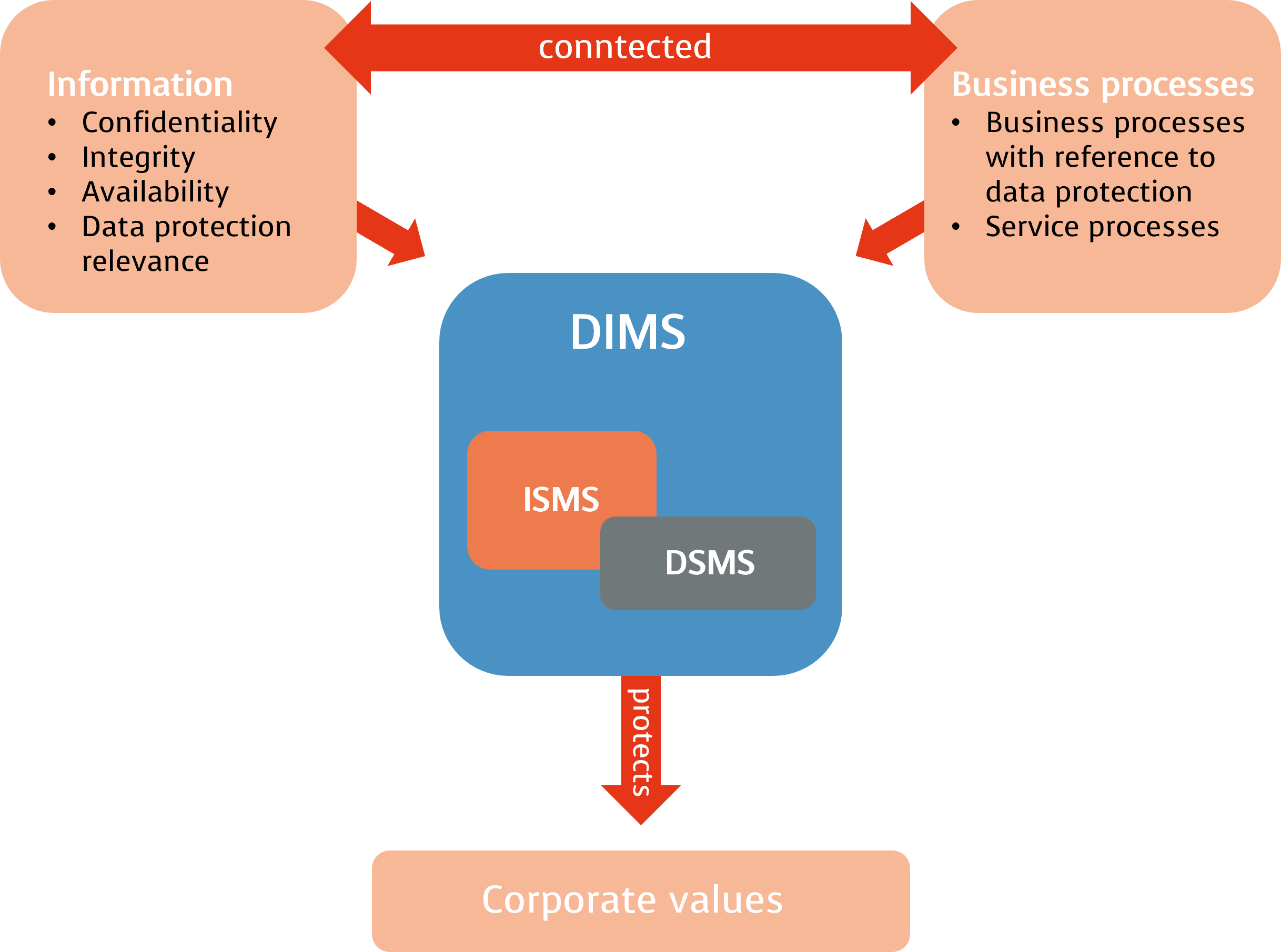
Data protection management process
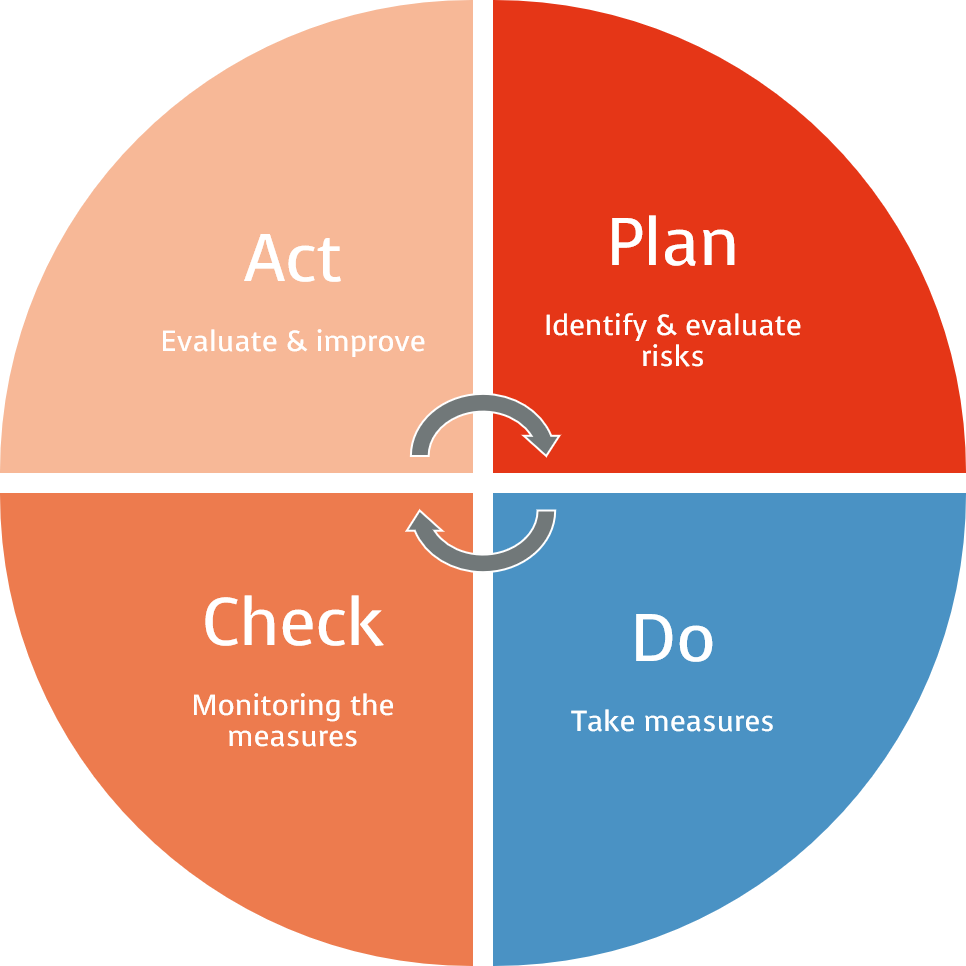
Functions of the DPMS
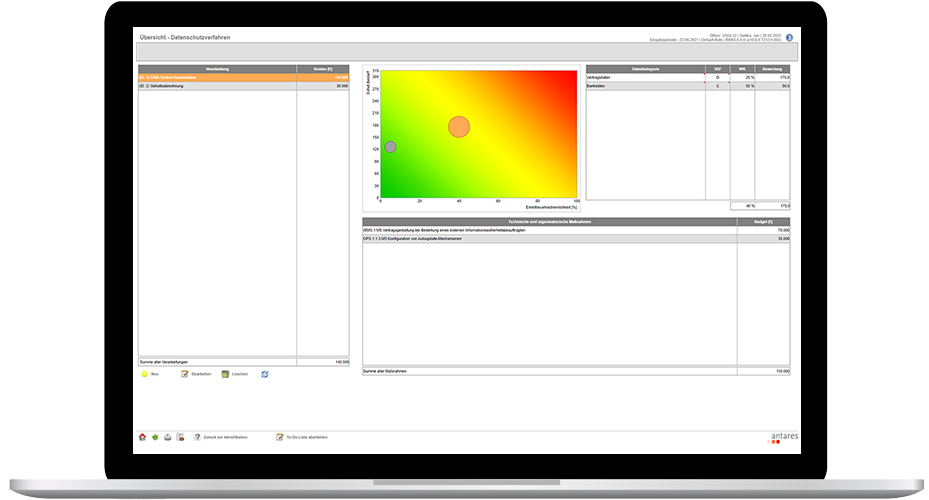
- Complete and audit-proof documentation of all data protection and information security activities incl. directory of processing activities.
- Seamless integration of information and business processes that require protection.
- Improve the data protection organisation by integrating the General Data Protection Regulation (GDPR) into an ISMS.
- Compliance with all data protection and information security requirements.
- In the event of an audit, meet the accountability obligations of the basic regulation towards supervisory authorities and escape fines.
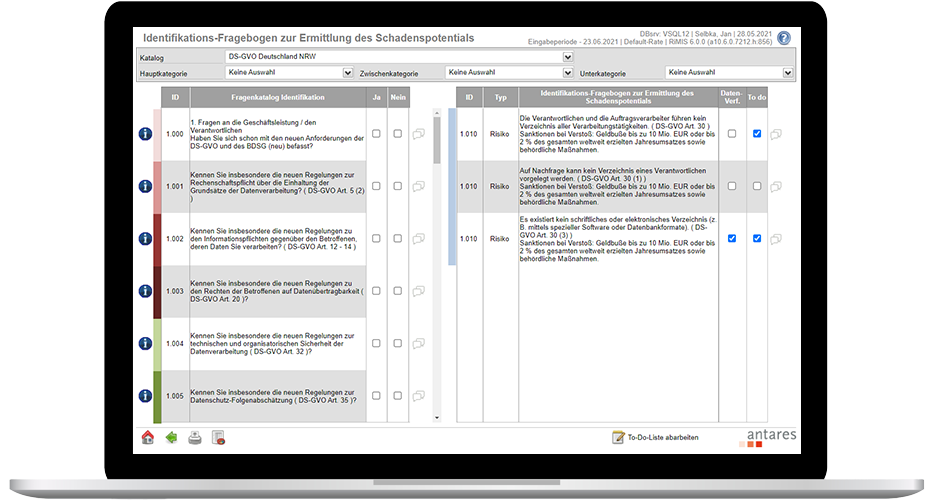
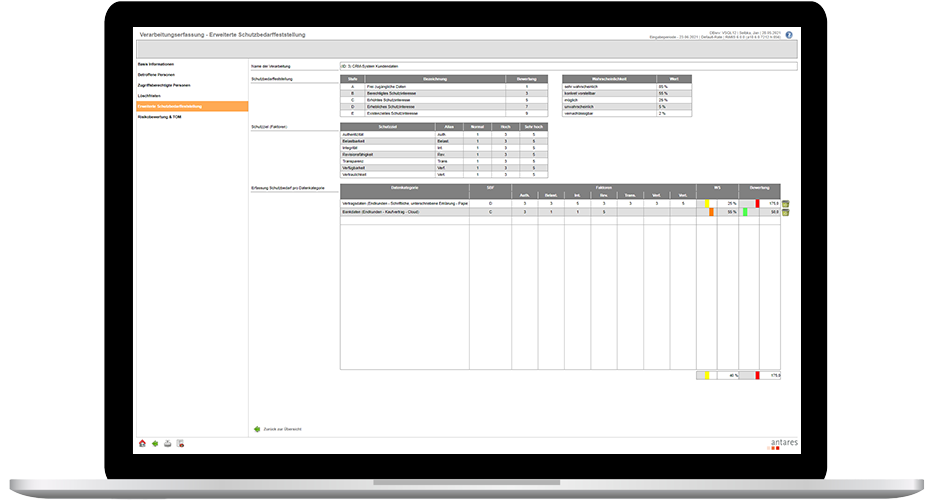
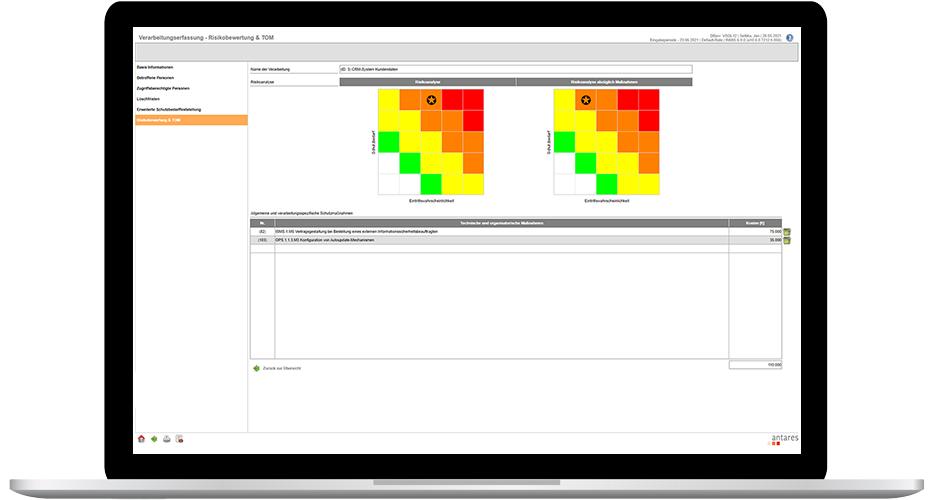
- Protection needs analysis and risk assessment, including the data protection risk management measures derived from it.
We are a licensed manufacturer of IT baseline tools.

Extract from our references






Data protection management compact

Confidentiality
Confidential information must be protected from unauthorised access. Prevent information from falling into the wrong hands due to vulnerabilities in the system, neither accidentally nor intentionally as well as only being available to authorised persons.

Integrity
Ensure that IT systems, IT procedures and information are accurate, tamper-free, intact and authentic. The authenticity, accountability and credibility of your information is considered in every process.

Availability
Services and functions of an IT system or even information and relevant documents are always available at the specific, required time.

ISO 27001 certification
We support you with certification according to ISO/IEC 27001 and on the basis of IT baseline. Certification shows that your company has taken appropriate measures to secure the IT systems and thus the company's data.

IT baseline certification
We support you with certification according to BSI IT baseline. This offers assistance with the introduction and maintenance of an information security management system. Since 2006, the IT baseline catalogue has been adapted to the international standard ISO/IEC 27001.

Construction
Our software solution is multi-client and web-enabled, so that every user can access the data regardless of time and location. Scalability and the assignment of authorisation roles ensure optimal user guidance. The intuitive interface helps to save valuable time and increases the speed of response.
FAQ
Why is it advisable to integrate the requirements of the General Data Protection Regulation into a DSMS?
The integration ensures that all relevant requirements of the GDPR are implemented demonstrably and transparently.
Can country-specific requirements and legislation be taken into account?
Yes, this can be mapped in the solution via special questionnaires and checklists.
Is a risk impact assessment included in the software process?
Yes, risk impact assessment can be carried out in several ways. These include, for example, scenarios, monetary or qualitative assessment methods, and temporal allocations.
Where can I find the complete version of the GDPR?
The complete version of the GDPR with all innovations regarding the principles and obligations for the processing of personal data, data subject rights, commissioned processing, data protection impact assessment, obligation to provide evidence, directory of processing activities to be kept by a controller, etc. can be found here.
Download
Improve your data protection organisation and incorporate the General Data Protection Regulation (GDPR) into an ISMS to benefit from the numerous advantages of a holistic data protection management system.
Arrange initial meeting now

Jochen Brühl | Managing director
Select your desired option and arrange a non-binding and free consultation with our managing director Jochen Brühl.
We will answer your questions and make sure that you get to know our software in detail. We will be happy to show you the solution to your individual requirements. Afterwards, if you wish, we will present the performance spectrum of our software to you, live and directly, via web session or personally at your premises.
Information on data protection