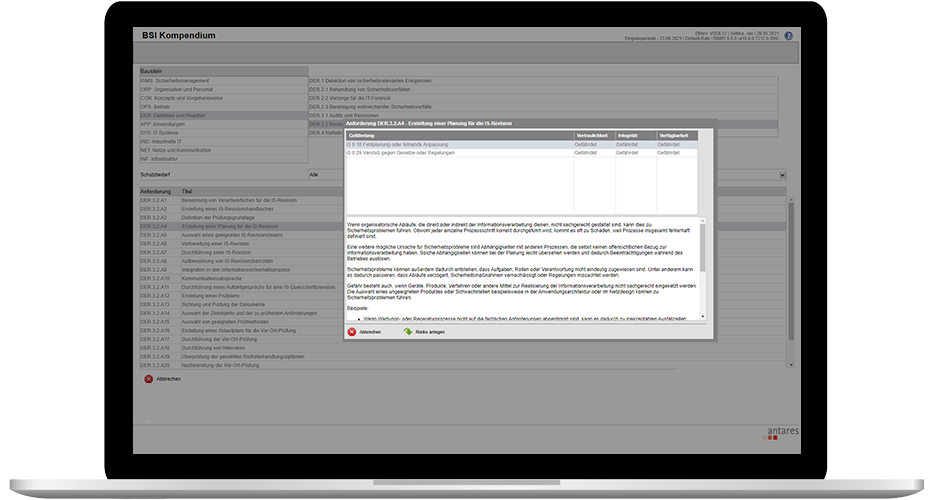
antares RiMIS® ISMS
Our ISMS establishes procedures and rules in accordance with ISO 27001 in the company in order to permanently manage, control, maintain and continuously improve information security. With the help of the application, information security risks can be identified, evaluated and reduced in a targeted manner. Use antares RiMIS® ISMS as a reliable information base to derive important protective measures and to introduce an information security culture in your company.
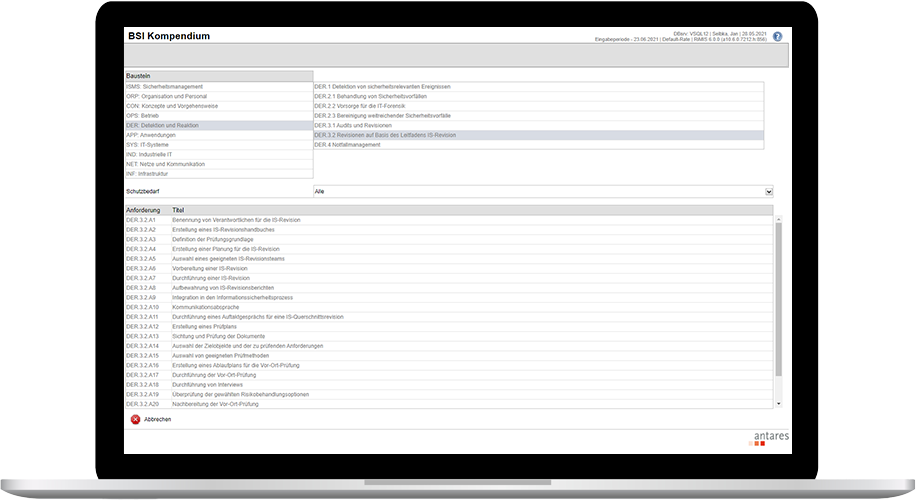
For automotive manufacturers and suppliers aiming at a TISAX® certification, we provide antares RiMIS® ISMS with integrated VDA ISA catalog as well as the BSI basic protection catalog. Thus, weak points can be identified and identified gaps can be closed before the start of the audit.

Management system for information security

ISO 27001 & BSI IT baseline certification

Ensuring the protection goals

Assignment of authorisation roles

Decentralised access thanks to web capability
Functions of the ISMS
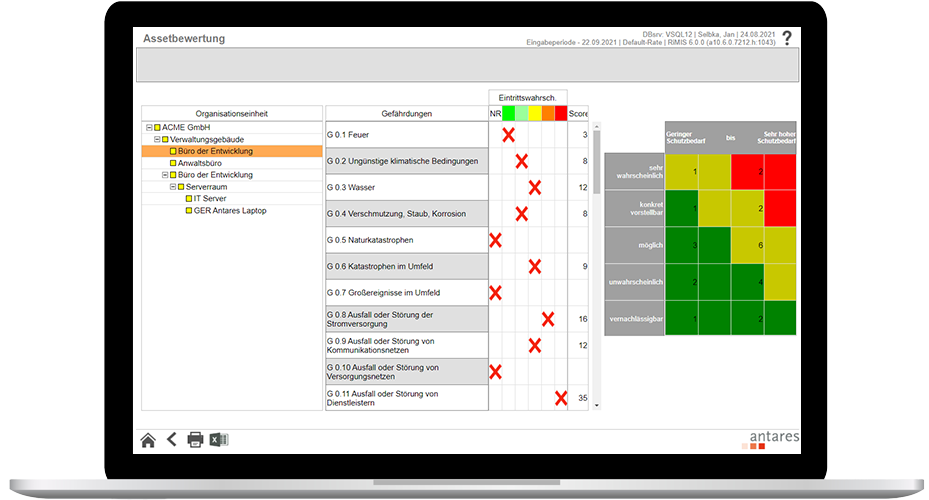
- Identify vulnerabilities, detect threats, document them and take countermeasures.
- Protective measures can be tracked and traced.
- Raise awareness of information security throughout the company.
- Involvement of employees, departments and responsible persons in the ISMS process.
- For automotive suppliers and OEMs: Extension with the integrated VDA ISA catalogue.
- System provides assistance at management level.
- Target group related documentation.
- Possibility of modifying the tool.
- Problem-free adaptation of the software to individual requirements and processes.
- Modular expandability leads to investment security (return on security investment).
We are a licensed manufacturer of IT baseline tools.

Extract from our references






Information security management compact

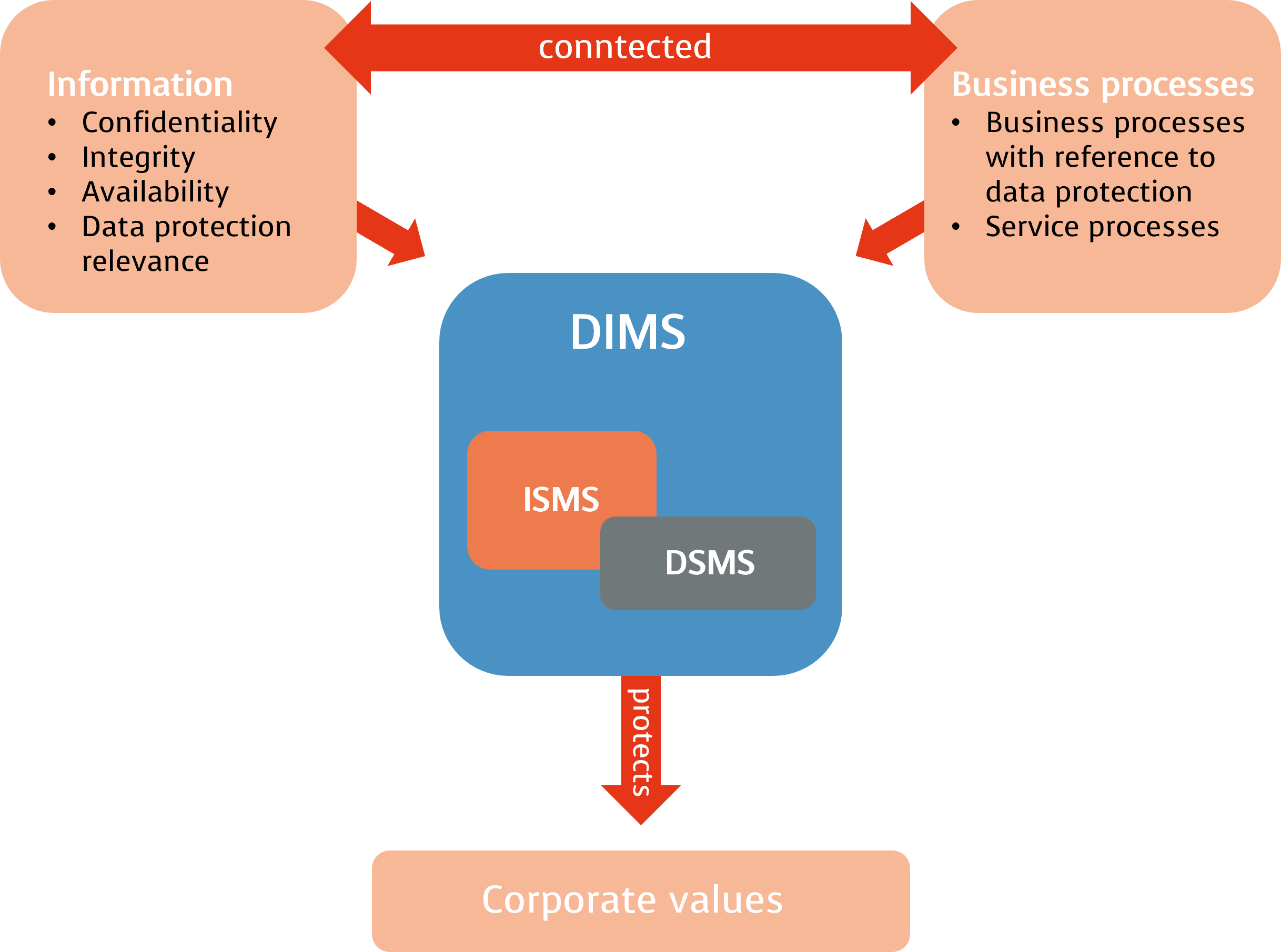
Confidentiality
Confidential information must be protected from unauthorised access. Prevent information from falling into the wrong hands due to vulnerabilities in the system, neither accidentally nor intentionally as well as only being available to authorised persons.

Integrity
Ensure that IT systems, IT procedures and information are accurate, tamper-free, intact and authentic. The authenticity, accountability and credibility of your information is considered in every process.

Availability
Services and functions of an IT system or even information and relevant documents are always available at the specific, required time.

ISO 27001 certification
We support you with certification according to ISO 27001 and on the basis of IT baseline. Certification shows that your company has taken appropriate measures to secure the IT systems and thus the company's data.

IT baseline certification
We support you with certification according to the BSI IT baseline. This offers assistance with the introduction and maintenance of an information security management system. Since 2006, the IT baseline catalogue has been adapted to the international standard ISO/IEC 27001.

Construction
Our software solution is multi-client and web-enabled, so that every user can access the data regardless of time and location. Scalability and the assignment of authorisation roles ensure optimal user guidance. The intuitive interface helps to save valuable time and increases the reaction speed.
A secure grip on data protection
With the IT Security Act and the data protection regulation, the topic of information security and data protection in information technology has gained in importance. In order to master the requirements in the company, it makes sense to integrate the data protection guidelines into the existing information security management system (ISMS). By integrating the data protection topic into the existing ISMS, a holistic data protection management system (DPMS) is created.
FAQ
Does the software solution offer the possibility to support the ISMS process via standard catalogues and industry-specific checklists?
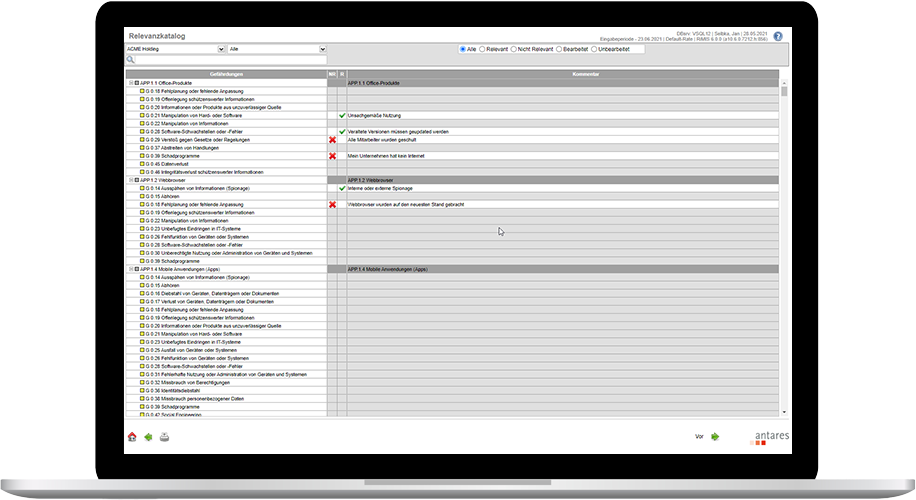
The integration of standard catalogues, such as the BSI basic protection catalogue, is already provided for in the software. In addition, sector-specific catalogues are available, such as the ISMS requirements from the TISAX® sector.
Can an asset structure be mapped?
Yes, an asset structure can be integrated as flexibly as desired via the stored structure trees. The structure can also be set up via interfaces to upstream systems.
Is it possible to deactivate information security areas that are not relevant?
Yes, these areas can be marked accordingly via the company/asset structure.
Is there a reporting module for monitoring the ISMS process?
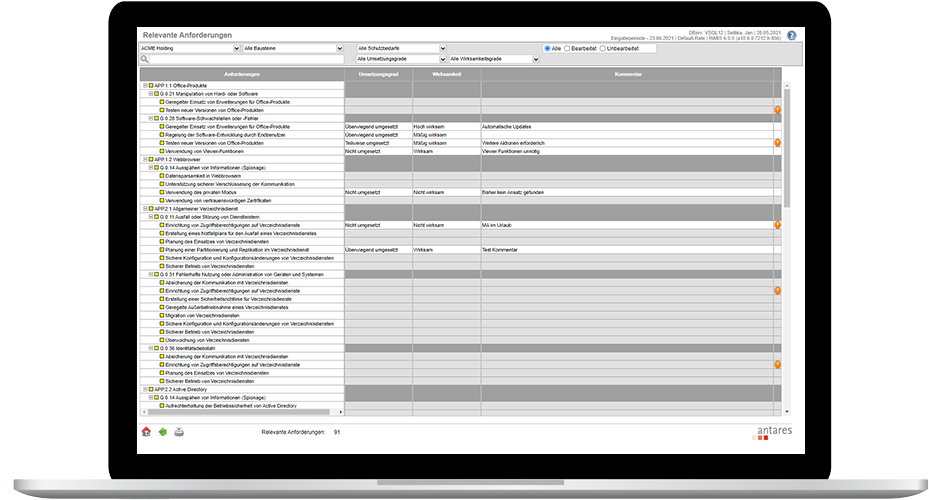
Yes, within the solution there are various status overviews, dashboards and evaluations about the status of the process and the degree of fulfilment.
Is it possible to integrate external documents and files?
Yes, this can be realised via attachments as well as via links.
Do you also offer organisational consulting services?
Yes, we have specialists with many years of practical experience in a wide range of industry sectors.
Download
Establish procedures and rules according to ISO 27001 in the company to permanently improve information security and be prepared for disruptions and IT security incidents. The most important functions of the ISMS module can be found in our product flyer.
Arrange initial meeting now

Jochen Brühl | Managing director
Select your desired option and arrange a non-binding and free consultation with our managing director Jochen Brühl.
We will answer your questions and make sure that you get to know our software in detail. We will be happy to show you the solution to your individual requirements. Afterwards, if you wish, we will present the performance spectrum of our software to you, live and directly, via web session or personally at your premises.
Information on data protection